Reverse Engineering Documents (Archived)In 2007, I decided to write some documents about reverse engineering for educational purposes. I created various software for different cases and cracked my own software to show examples. I wrote 11 documents about reverse engineering in total.
Reverse engineering was a quite funny hobby for me in these years. I also participated in some cracking competitions and won first place. But, as a software developer, I primarily focus on protection techniques against reverse engineering. If you create something new, protecting your intellectual property means so much to you. There is not only a software piracy threat, there are also some people who modify your work or steal your valuable algorithms. So, software developers should know how to protect their software. If you designed an online system, your customers also might be harmed because of this reason.
I worked in this area, professionally in the defense industry and I designed and implemented a software protector against reverse engineering for the x86, x64 Windows operating systems, and the Linux distros. This is not a common area. So, I also worked on other projects after this.
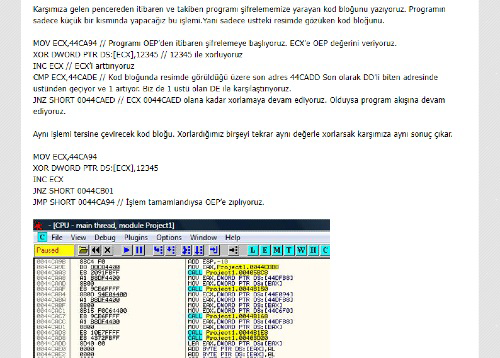
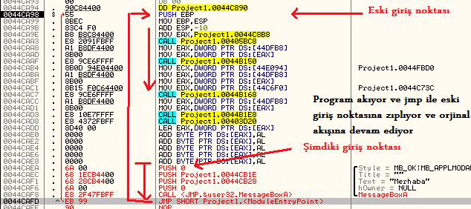
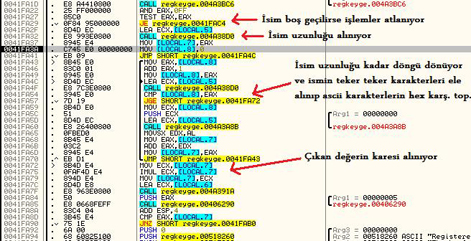
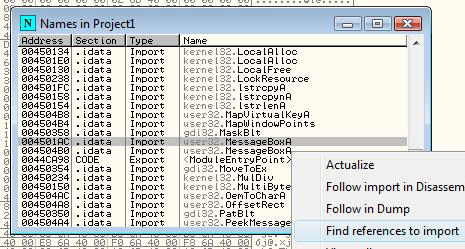
My reverse engineering documents are in the Turkish language and they are quite old after 15 years. They belong to my late high school years. I made some decisions. I am completely translating my website into the English language and removing very old content. So, I decided to remove them in 2023.
This is a lifetime hobby for me. But it is not my primary hobby either. Software protection never ends. It is a mouse and cat game like the antivirus industry. Maybe someday I may write new documents and develop new projects about reverse engineering. But, today, I have no plan for this.
I wrote 11 reverse engineering documents,
1. Making a Game Trainer
2. Code Injection
3. Making a Key Generator
4. Unpacking and Rebuilding PE
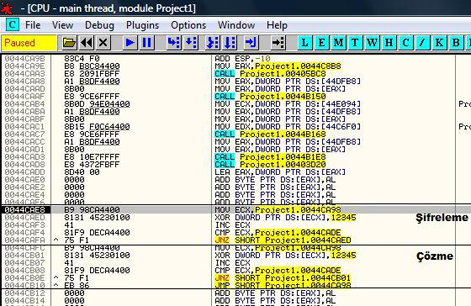
5. Self-modifying Executables
6. Finding The Target Code
7. Making a Patcher
8. Reverse Engineering Delphi Executables
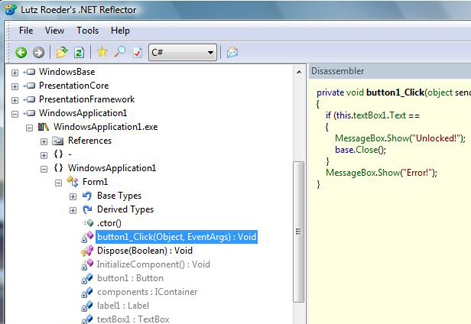
9. Reverse Engineering .Net Executables
10. Reverse Engineering VB and VB P-Code Executables
11. Software Protection Techniques against Reverse Engineering
 |

